Step up your authentication game

Consider the case of a buyer making a large purchase
Get ready to code!
Follow along using
Node.js
Your
favorite IDE
Terminal
window
Browser
Authentication is an expectation
Delegate to an Identity Provider
OAuth 2.0
OpenID Connect
Delegate to an Identity Provider
OAuth 2.0
AuthorizationOpenID Connect
AuthenticationIdentity Provider manages authentication


Getting going
Time to code
- Get Tour of Heroes project from alisaduncan/angular-stepup-auth
- Install dependencies with
npm ci - Run app locally using
npm start - Log in and sign up using password and email verification
Authentication may not be enough
We treat authentication equally across applications, and use authorization for access control.
But should we?
It's time to treat authentication with more granularity than true or false
RFC 9470 OAuth 2.0 Step Up Authentication Challenge
Elevate authentication factors
Enforce recent authentication
Step Up Authentication Challenge


Guard a route
export const myGuard: CanActivateFn = (route, state) => {
return true;
};export const routes: Routes = [
{
path: 'protected',
component: MyComponent,
canActivate: [myGuard]
},
...,
];Protect the admin route
- Add a
stepUpGuardinauth.guard.tsfile - Prevent route navigation by returning
false - Add the step up guard to the
"/admin"route
OAuth 2.0 + OpenID Connect
The snorkeler's view of the protocols
Snorkeling in the bay of
OAuth 2.0 + OpenID Connect
OAuth 2.0
OpenID Connect
Snorkeling in the bay of
OAuth 2.0 + OpenID Connect
OAuth 2.0
- Authorization
- Access token
OpenID Connect
- Authentication
- ID token
The Access and ID tokens are JSON Web Token (JWT) format
The Access and ID tokens are JSON Web Token (JWT) format
{
"claimKey": "claimValue"
}The Authentication Context Class Reference (ACR) define business rules identifying levels of assurance profiles
ACR value in token
{
"iss": "https://as.example.net",
"sub": "someone@example.net",
"aud": "https://rs.example.com",
"exp": 1646343000,
"iat": 1646340200,
"jti" : "e1j3V_bKic8-LAEB_lccD0G",
"client_id": "s6BhdRkqt3",
"scope": "purchase",
"auth_time": 1646340198,
"acr": "myACR"
}Step up auth in action
Step up auth in action
Step up auth in action



Step up auth in action
Step up auth in action
Step up auth in action

{
"iss": "https://as.example.net",
"sub": "someone@example.net",
"aud": "https://rs.example.com",
"exp": 1646343000,
"iat": 1646340200,
"jti" : "e1j3V_bKic8-LB_lDG",
"client_id": "s6BhdRkqt3",
"scope": "purchase",
"auth_time": 1646340198,
"acr": "low-ACR-level"
}Step up auth in action



Step up auth in action
Authentication Context Class Reference (ACR)
- Supports standard values and custom registries
- Examples include
phrfor phishing-resistant,phrhfor phishing-resistant hardware
Authentication Context Class Reference (ACR)
- Examples include
phrfor phishing-resistant,phrhfor phishing-resistant hardware - You may see ACR values such as
phr,http://schemas.openid.net/pape/policies/2007/06/multi-factor, andurn:okta:loa:2fa:any
Authentication Context Class Reference (ACR)
acr
The claim identifying the current authentication level.
acr_values
The requested authentication level.
acr_values_supported
ACR values supported by the authorization server. May be listed in the OIDC discovery document.
What about access control measures?
Access controls complement step up authentication challenge to better protect views and resources.
Step up authentication route guard
const authLevelMet = authService.acrClaim === ACR_VALUES_2FA; if (authLevelMet) return true; // continue navigation // else authenticate with required acr_values & redirect to URL authService.login(ACR_VALUES_2FA, currentURL); return false; // prevent navigation for now
const authLevelMet = authService.acrClaim === ACR_VALUES_2FA; if (authLevelMet) return true; // continue navigation // else authenticate with required acr_values & redirect to URL authService.login(ACR_VALUES_2FA, currentURL); return false; // prevent navigation for now
const authLevelMet = authService.acrClaim === ACR_VALUES_2FA; if (authLevelMet) return true; // continue navigation // else authenticate with required acr_values & redirect to URL authService.login(ACR_VALUES_2FA, currentURL); return false; // prevent navigation for now
const authLevelMet = authService.acrClaim === ACR_VALUES_2FA; if (authLevelMet) return true; // continue navigation // else authenticate with required acr_values & redirect to URL authService.login(ACR_VALUES_2FA, currentURL); return false; // prevent navigation for now
Finish step up guard implementation
- Get the
acrclaim from the ID token - Check claim matches the
acr_values - Call
authService.login()
Use route data to define ACR levels per route
What else can we protect?
It is not uncommon for resource servers to require different authentication strengths or recentness according to the characteristics of a request.
Protecting resources, not just views




Resource server error
HTTP/1.1 401 Unauthorized
WWW-Authenticate: Bearer error="insufficient_user_authentication",
error_description="A different authentication level is required",
acr_values="myACR"


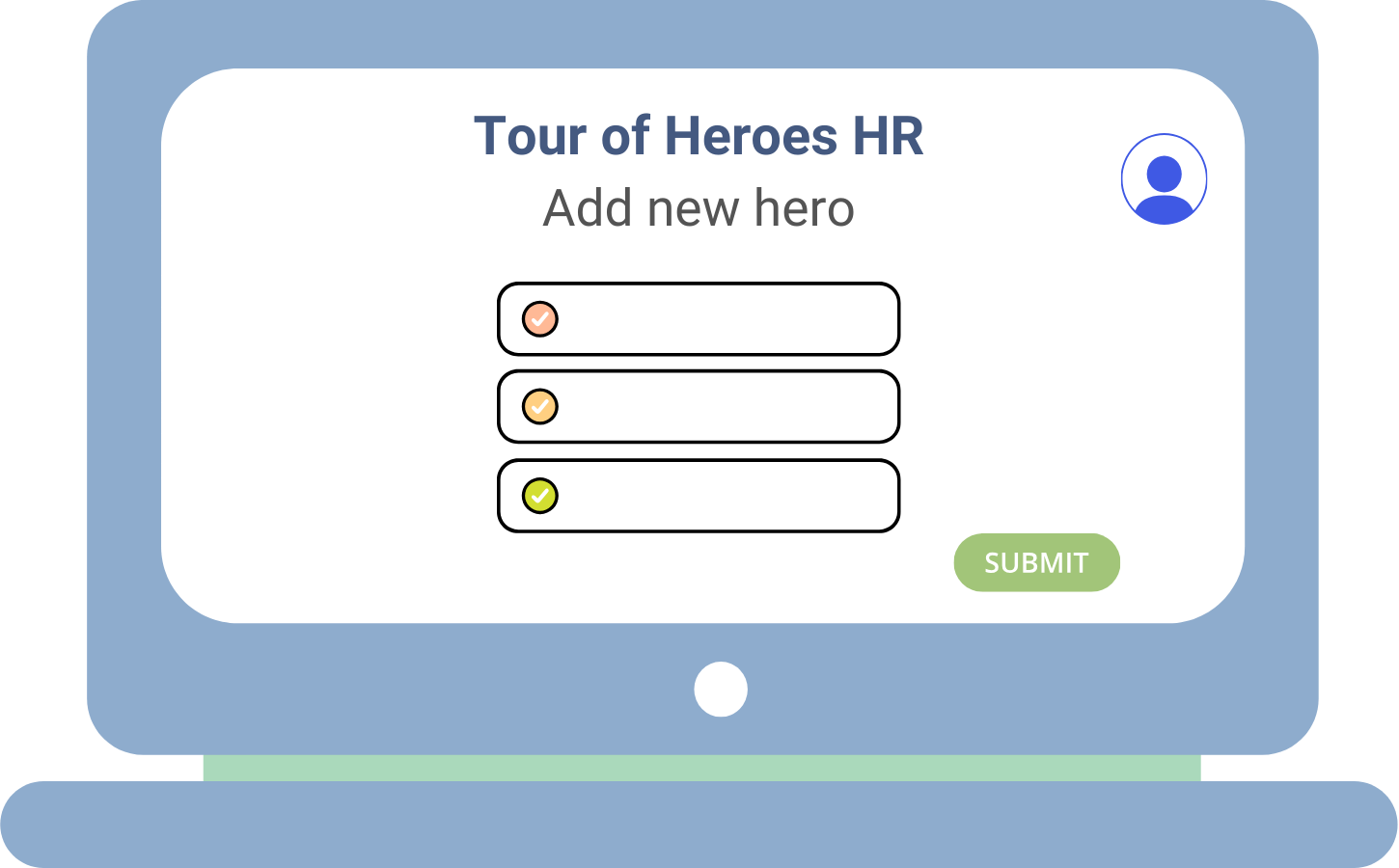
It's time we protect the heroes!
Enable step up middleware in API
- Add the
StepUpMiddlewareto routes - Review the middleware implementation
Handle the error response
The Angular app orchestrates authenticating and re-requesting resources.
Interceptors in Angular
Use an interceptor to format the HTTP response error into something we can handle within the app
Interceptors in Angular
export const stepupInterceptor: HttpInterceptorFn = (req, next) => {
return next(req).pipe(
catchError(handleError)
);
};Interceptors in Angular
const handleError = (httpError: HttpErrorResponse) => {
// verify origin url
// ensure error is 'insufficient_user_authentication'
// format a new Error with acr_values
};export const stepupInterceptor: HttpInterceptorFn = (req, next) => {
return next(req).pipe(
catchError(handleError)
);
};Responding to errors in services
export class HeroService {
private router = inject(Router);
private http = inject(HttpClient);
private authService = inject(AuthService);
getHeroes(): Observable<Hero[]> {
return this.http.get<Hero[]>('/api/heroes').pipe(
catchError(error => {
// handle step up auth error response
return throwError(() => error);
})
)
}
}Responding to step up auth error
- Ensure the
HttpErrorResponsecontains the step up auth error header - Pull key step up auth info from the error
- Authenticate with the required ACR values
- Re-request the resource
See the completed project
alisaduncan/angular-stepup-auth
Check out the completed branch
Congrats!
Let's talk about next steps!
If you use Okta, the Angular SDK has built-in stepup auth support.
What about recency?
- Replace
acr_valueswithmax_age - Calculate recency using
auth_timeclaim
Have good authentication security